Insider Threat

Insider Threat An insider threat is someone who works for or with your organization but has ulterior motives. Employees who steal your information are insider threats. Data Loss Prevention systems can be used to help identify insider threats. Warning! The biggest threat to organizational security is employees or contractors who have authorized access to company systems and data. While these people may have good intentions, they can also unintentionally introduce malware or leak sensitive information.
Domain Name Kiting
Domain Name Kiting Domain name kiting is an attack that exploits a flaw in the domain name registration process. This flaw allows the attacker to keep the domain name in limbo, preventing it from being registered by an authenticated buyer.
Pharming

Pharming Pharming occurs when an attacker reroutes a website’s traffic to a different, illegitimate site. This can be done in a variety of ways, such as DNS cache poisoning or domain hijacking. Pharming can be used to steal sensitive information like login credentials or financial information.
Man-in-the-Middle (MITM)
Man–in–the–Middle (MITM) An attacker who is able to intercept data flowing between two parties can “man-in-the-middle” the communication, causing data to flow through their own computer where they can view or manipulate it.
Clickjacking

Clickjacking A clickjacking attack uses multiple transparent layers to trick a user into clicking on a button or link on a page when they were intending to click on the actual page.
Watering Hole
Watering Hole This occurs when an attacker knows that his potential victims will access a certain website, and he places malware on that website in order to infect them.
Blind Hijacking

Blind Hijacking This type of attack is called “blind hijacking“ and it occurs when an attacker injects data into a communication stream without being able to see if the injection is successful or not.
TCP/IP Hijacking
TCP/IP Hijacking This happens when an attacker hijacks a TCP session between two machines without the use of a cookie or other host access.
Man-in-the-Browser (MITB)
Man-in-the-Browser (MITB) The browser hijacking attack occurs when a malicious actor modifies the web pages or transactions being done within a web browser, usually by infecting the browser with a Trojan horse. This can allow the attacker to steal sensitive information or redirect the victim to a malicious website.
Endpoint analysis
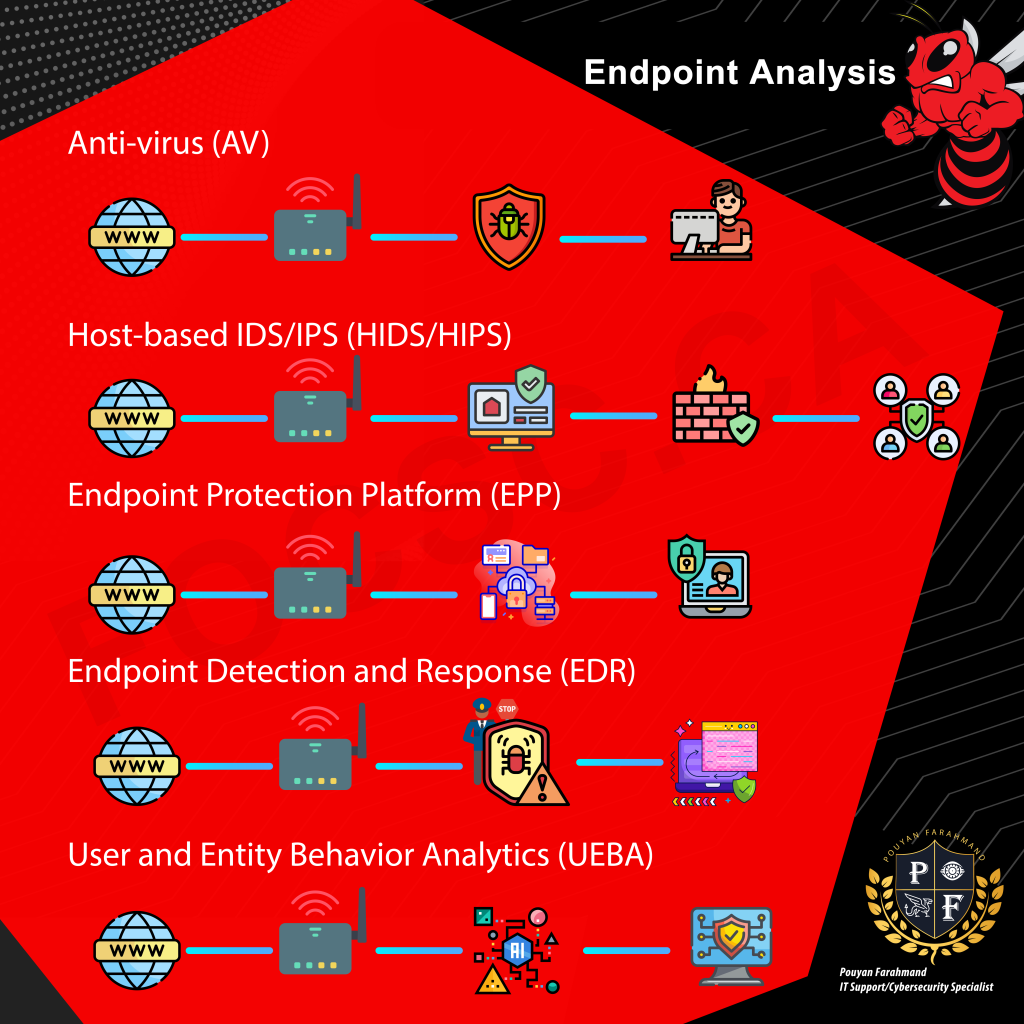
Endpoint analysis 1. Introduction Endpoint security is a vital part of any organization’s security posture. In this guide, we will discuss the various types of endpoint security solutions available and their key features. We will also provide an overview of the benefits and challenges associated with each solution. 2. Types of Endpoint Security Solutions There are a variety of endpoint security solutions available, each with its own advantages and disadvantages. The following are some of the most common types of endpoint security solutions: 3. Anti-Virus (AV) Anti-virus (AV) software is designed to detect and remove virus infections and other types of malware, such as worms, Trojans, rootkits, adware, spyware, password crackers, network mappers, DoS tools, and others. AV software typically uses a combination of signature-based and heuristic-based detection methods. Signature-based detection relies on a database of known malware signatures. When new malware is discovered, its signature is added to the database and AV software can then detect and remove any instances of that malware. Heuristic-based detection looks for suspicious behavior that may be indicative of malware. AV software is a common type of endpoint security solution, but it has some limitations. First, AV software can only detect malware that it already knows about. New malware can easily go undetected. Second, AV software can impact system performance, as it must constantly scan files for malware. 4. Host-Based IDS/IPS (HIDS/HIPS) A host-based IDS/IPS (HIDS/HIPS) is a type of IDS or IPS that monitors a computer system for unexpected behavior or drastic changes to the system’s state. HIDS/HIPS can be used to detect a variety of attacks, including viruses, worms, Trojans, rootkits, and buffer overflows. HIDS/HIPS typically use a combination of signature-based and heuristic-based detection methods. Signature-based detection relies on a database of known attack signatures. When new attacks are discovered, their signatures are added to the database and HIDS/HIPS can then detect and block any instances of those attacks. Heuristic-based detection looks for suspicious behavior that may be indicative of an attack. HIDS/HIPS is a powerful endpoint security solution, but it has some limitations. First, HIDS/HIPS can only detect attacks that it already knows about. New attacks can easily go undetected. Second, HIDS/HIPS can impact system performance, as it must constantly monitor system activity for suspicious behavior. 5. Endpoint Protection Platform (EPP) An endpoint protection platform (EPP) is a software agent and monitoring system that performs multiple security tasks, such as anti-virus, HIDS/HIPS, firewall, DLP, and file encryption. EPP solutions typically use a combination of signature-based and heuristic-based detection methods. Signature-based detection relies on a database of known malware signatures. When new malware is discovered, its signature is added to the database, and EPP can then detect and remove any instances of that malware. Heuristic-based detection looks for suspicious behavior that may be indicative of malware. EPP is a comprehensive endpoint security solution, but it has some limitations. First, EPP can only detect malware that it already knows about. New malware can easily go undetected. Second, EPP can impact system performance, as it must constantly scan files for malware. 6. Endpoint Detection and Response (EDR) An endpoint detection and response (EDR) system is a software agent that collects system data and logs for analysis by a monitoring system. EDR can be used to detect a variety of attacks, including viruses, worms, Trojans, rootkits, and buffer overflows. EDR typically uses a combination of signature-based and heuristic-based detection methods. Signature-based detection relies on a database of known attack signatures. When new attacks are discovered, their signatures are added to the database, and EDR can then detect and respond to any instances of those attacks. Heuristic-based detection looks for suspicious behavior that may be indicative of an attack. EDR is a powerful endpoint security solution, but it has some limitations. First, EDR can only detect attacks that it already knows about. New attacks can easily go undetected. Second, EDR can impact system performance, as it must constantly monitor system activity and collect data for analysis. 7. User and Entity Behavior Analytics (UEBA) User and entity behavior analytics (UEBA) is a system that can provide an automated identification of suspicious activity by user accounts and computer hosts. UEBA solutions are heavily dependent on advanced computing techniques like artificial intelligence (AI) and machine learning. UEBA is a powerful endpoint security solution, but it has some limitations. First, UEBA can only detect suspicious activity that it already knows about. New attacks can easily go undetected. Second, UEBA can impact system performance, as it must constantly monitor system activity and collect data for analysis. 8. Conclusion Endpoint security is a vital part of any organization’s security posture. There are a variety of endpoint security solutions available, each with its own advantages and disadvantages. The best solution for your organization will depend on your specific needs and requirements.
