Hashcat
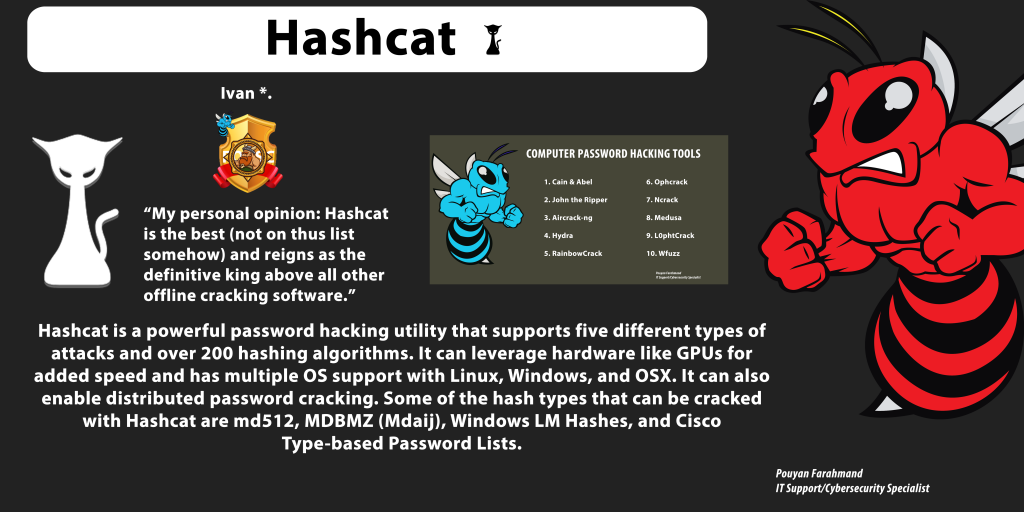
Hashcat is a powerful password hacking utility that supports five different types of attacks and over 200 hashing algorithms. It can leverage hardware like GPUs for added speed and has multiple OS support with Linux, Windows, and OSX. It can also enable distributed password cracking. Some of the hash types that can be cracked with Hashcat are md512, MDBMZ (Mdaij), Windows LM Hashes, and Cisco Type-based Password Lists. Pouyan Farahmand #hashcat #password #hacking #linux #windows #cisco #algorithms
TOP 10 HACKING TOOLS
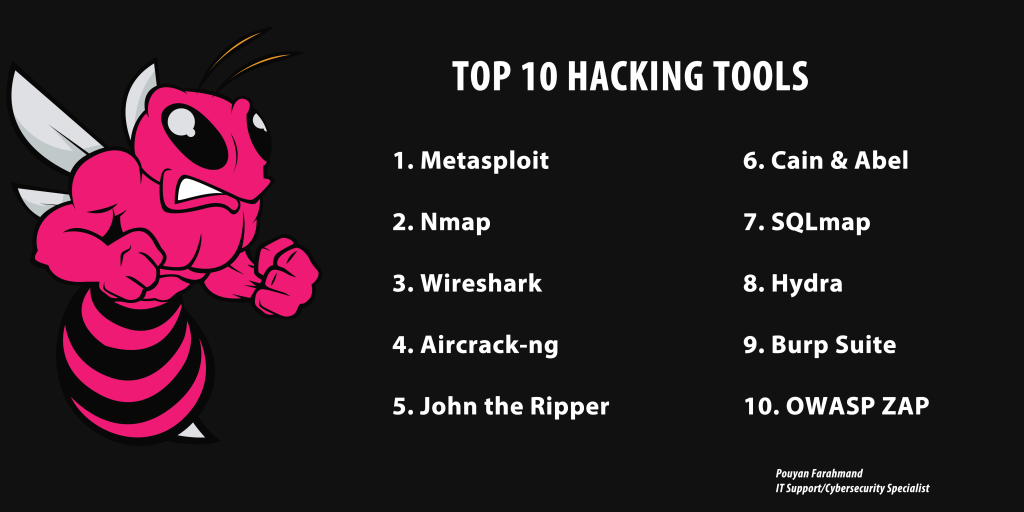
1. Metasploit 2. Nmap 3. Wireshark 4. Aircrack-ng 5. John the Ripper 6. Cain & Abel 7. SQLmap 8. Hydra 9. Burp Suite 10. OWASP ZAP Pouyan Farahmand #hacking #hackingtools #metasploit #nmap #wireshark #Aircrack-ng #JohntheRipper #CainAbel #SQLmap #Hydra #burpsuite #OWASPZAP
WHY WE NEED HACKERS!

1. Hackers can help to identify security vulnerabilities in systems and networks. 2. Hackers can help to protect against potential attacks by identifying and exploiting weaknesses. 3. Hackers can help to improve system security by finding and reporting flaws. 4. Hackers can help to raise awareness of security issues and promote best practices. 5. Hackers can help to ensure the safety and security of systems and data.
COMPUTER PASSWORD HACKING TOOLS!

1. Cain & Abel 2. John the Ripper 3. Aircrack-ng 4. Hydra 5. RainbowCrack 6. Ophcrack 7. Ncrack 8. Medusa 9. L0phtCrack 10. Wfuzz #hacking #password
What is Ransomware?
Ransomware is a type of malware that encrypts a victim’s files and demands a ransom be paid in order to decrypt them. Ransomware is usually spread through phishing emails or by exploit kits that take advantage of vulnerabilities on a victim’s computer. Once a computer is infected with ransomware, the victim’s files are typically encrypted with a strong encryption algorithm making them inaccessible. A ransom note is then displayed on the victim’s computer screen with instructions on how to pay the ransom and decrypt the files. In some cases, paying the ransom does not guarantee that the victim’s files will be decrypted. There have been instances where the ransomware developers demand more money after the initial ransom has been paid, or they may simply not provide the decryption key after payment has been made. It is important to note that paying the ransom does not guarantee access to the encrypted files and should only be considered as a last resort. How to Protect Yourself from Ransomware The best way to protect yourself from ransomware is to have a robust backup strategy in place. This way, if your computer is infected with ransomware, you can simply restore your files from backup and not have to worry about paying the ransom. There are a few other things you can do to protect yourself from ransomware: • Keep your operating system and software up to date: Install security updates as soon as they are released • Use an antivirus: A good antivirus program can detect and block many ransomware infections • Be careful what you click: Don’t open email attachments from people you don’t know and be cautious about the links you click • Enable popup blockers: Some ransomware is spread through malicious websites that display popup ads. Popup blockers can help prevent these ads from being displayed What to Do if You’re Infected with Ransomware If you think your computer has been infected with ransomware, the first thing you should do is disconnect it from the internet to prevent the ransomware from spreading to other computers on your network. Next, you will need to scan your computer with an antivirus program to remove the ransomware. Once the ransomware has been removed, you can then restore your files from backup. If you don’t have a backup of your files, you may need to pay the ransom in order to get the decryption key. However, as we mentioned before, there is no guarantee that you will get the decryption key even if you pay the ransom. So, paying the ransom should only be considered a last resort. Ransomware is a type of malware that encrypts a victim’s files and demands a ransom be paid in order to decrypt them. Ransomware is usually spread through phishing emails or by exploit kits that take advantage of vulnerabilities on a victim’s computer. Once a computer is infected with ransomware, the victim’s files are typically encrypted with a strong encryption algorithm making them inaccessible. A ransom note is then displayed on the victim’s computer screen with instructions on how to pay the ransom and decrypt the files.
Hackers!
Hackers are not always bad. In fact, there are many good hackers out there who use their skills to help people. Most people think of hackers as criminals who steal information or wreak havoc on computer systems. But there are also many ethical hackers who use their hacking skills for good. Ethical hackers are also known as white hat hackers. They use their hacking skills to find security vulnerabilities in systems and help businesses and organizations fix those security issues. Many ethical hackers are also security researchers who help companies create better security systems. They also help raise awareness about security issues and educate people about how to protect themselves from cyber threats. There are even some ethical hackers who work for law enforcement agencies and help them track down criminals. So, the next time you think of a hacker, don’t automatically assume that they’re a bad person. There are many good hackers out there who are using their skills to help people.
What NOT to do After You’ve Been Hacked!

1. Don’t panic! 2. Don’t try to fix things yourself – you could make them worse. 3. Contact your local police department and let them know what happened. 4. Contact your bank or credit card company and let them know what happened. 5. Change all of your passwords – and make sure they are strong! 6. Keep an eye on your credit report and watch for any suspicious activity. 7. Be extra careful with email and social media – don’t click on any links or open any attachments from people you don’t know. 8. Do not ignore the problem.
HACKER

Some people use their computer skills to break into other people’s systems. This is called “hacking.” Hackers can do things like steal personal information or money, or cause problems with important computer systems. Hackers are usually very good at using computers, and they are always finding new ways to break into systems. That’s why it’s important to have good security on your computer and to keep your system and software up-to-date.
Most Common Computer Viruses
There are many types of computer viruses, but some of the most common are: • Boot sector virus – A virus that infects the boot sector of a hard drive or floppy disk. This type of virus is often spread by floppy disks that are left in the disk drive. • File infector virus – A virus that infects executable files. When the infected file is run, the virus is also run. This type of virus is often spread by email attachments or by downloading infected files from the Internet. • Macro virus – A virus that is written in a macro language. Macro viruses are often spread by email attachments or by downloading infected files from the Internet. • Memory resident virus – A virus that stays in memory and infects files when they are accessed. This type of virus is often spread by email attachments or by downloading infected files from the Internet. • Script virus – A virus that is written in a scripting language. Script viruses are often spread by email attachments or by downloading infected files from the Internet.
5 things to do after being hacked!
1. Don’t panic! Take a deep breath and assess the situation. 2. Change all of your passwords, especially for any accounts that may have been compromised. 3. Run a virus scan on your computer to check for any malicious software. 4. Notify your friends, family, and any other contacts that may have been affected. 5. Stay vigilant in the future and keep your computer security up-to-date.
